What is Decentralized Identity and Why Should You Care ?
Identity for the future - Own your identity, control your data.
Decentralized identity is a new form of user-centric digital identity also referred to as “self-sovereign identity”. It enables and empowers users to easily authenticate themselves to online services and share information in a privacy-conscious manner. Users can store, validate, produce and safe-guard their own identity information and associated data with ease. They have complete control over what they want to share, when, and with whom.
Why is it called decentralized identity ? Because it is not created or controlled by any online service or organization. Users create it, they own it and use it entirely on their own free will.
Sounds too good to be true ? Too futuristic ? Brace yourselves… decentralized identity is here and will disrupt the identity space even before you know it.
To understand the true benefits and power of decentralized identity, let’s look at what is wrong with how we interact with today’s identity systems and online services.
There are lots of things that are broken with today’s online interactions and I promise none of the points listed below will feel alien to you…
Identity Siloes — How many times do you tear your hair out when you need a use a new online service, and the site asks you to Sign Up ? Sound familiar ? This is a frustrating experience that we all put up with day in and day out. This is however key information needed by the online service to identify the user. For example, if it is a mail service, it needs to identify and authenticate the user before it can show the correct inbox page. Similarly other services also need to identify the user to render customized content.
Federated Login — The identity siloes are largely alleviated by using federated login providers such as Google, Facebook, Twitter, etc.; their credentials can be used instead of creating a new username and password for every new online service that you visit. With federated login, Google, Facebook and Twitter act as identity providers to the online service that the user is trying to sign-up to. The big disadvantage is these entities are aware of every online service the user is interacting with thereby sacrificing privacy for the convenience. The user still needs to remember which federated account was used to sign in to every online service, which in itself is a challenge when dealing with 100+ accounts. Some services like your banks and financial institutions cannot rely on federated login.
Password Hell — Apart from having to memorize hundreds of passwords, we need to keep changing them when they expire, adhere to complex password rules that differ per online service and devise mechanisms to remember them or like most users do — write them all on a piece of paper and leave them under the keyboard (No !!!). Most users also end up using the same password or have simple variations of the same password that can easily be hacked via brute-forcing and credential stuffing. This leaves accounts vulnerable to cyber attacks and we don’t have a solution to the problem. Now can you imagine the security implications if the password to your federated login account is compromised?
Password Leaks — How many times do you read news articles about breached usernames and passwords? Well, here are a few recent ones Webkinz, Zoom, GateHub, EpicBot, Activision. Though passwords are stored hashed most of the time, you will be surprised how such basic security measures are bypassed even in today’s online systems. Most websites do not enforce strong passwords and therefore weak passwords can easily be guessed by hackers with the help of rainbow tables. Credential stuffing then allow hackers to use these passwords against other online services which might use the same username and password.
Onboarding Users — Many online services need the legitimate real-world identity of users to offer certain services — these could be the passport office where user is applying for a new passport, a user trying to open a bank account or applying for a new driver’s license to name a few scenarios. Such services require you to often upload scanned copies of your supporting documents that can prove your real-world identity and other related information. This in today’s world is a tedious, repetitive, manual process where the user has to fill in information into lengthy multi-page forms. This process is friction-laden and repetitive and results in delays and large costs in customer identity verification. Banks for example spends billions of dollars every year in customer KYC checks. Ever travelled to a country frequently that requires you to apply for a visa that is only valid for the dates of travel ? The lengthy visa applications can give anyone a migraine… (Phew!!)
Can decentralized identity solve these problems ? YES !!!! And it can do much more …. Here’s how it works in a nutshell…
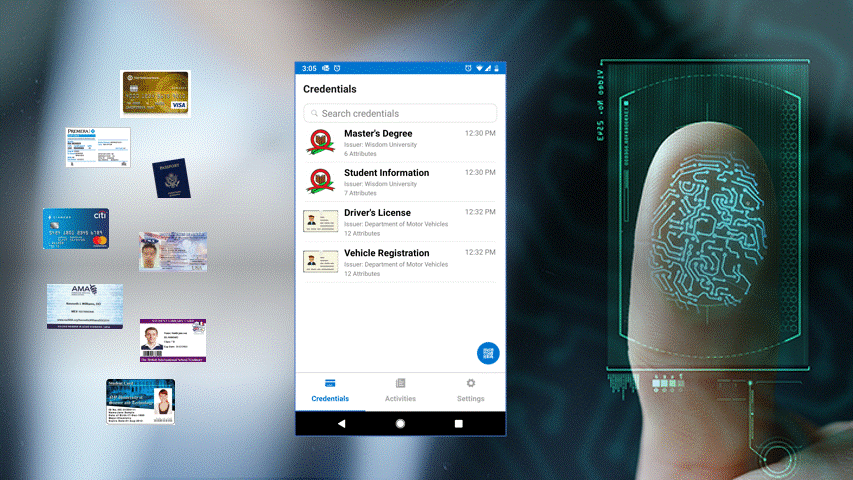
With decentralized identity, users use an identity wallet — an app on their phones that works like any other app except it has a high level of security. In the setup phase, users create their own identity known as a decentralized identifier or DID for short. It is a unique identifier for the user just like a username. The cryptographic material generated to protect this identity are called cryptographic keys that are equivalent to a password but have much stronger security guarantees. The keys are safeguarded on the user’s phone and can only be unlocked by the user with his biometrics when using the identity wallet app. The keys are used in interactions with online services where they can sign transactions on behalf of the user. This is how the online service can verify and authenticate the user i.e. by checking the signature on the transaction.
The identity wallet also stores verifiable credentials. These credentials are created and signed by issuers. Typical issuers can be government organizations, educational institutions, banks, financial institutions, telcos, visa offices, and so on — pretty much any public organization that in real life issues credentials like passports, licenses, educational certificates, SIM cards, visas, etc. With decentralized identity, they will issue these credentials digitally in the form of verifiable credentials. These credentials and all information within them can be stored inside users’ identity wallets.
Users can digitally present these credentials to verifiers. Verifiers are other public institutions that can digitally request and verify the presented credentials. This is equivalent to user producing driver’s license as proof to open a bank account or a user producing his passport and bank statement for a visa application. Interactions between users and verifiers can lead to quick one-tap digital verifications where the verifier can verify the signature of the issuer and confirm its authenticity. This way documents cannot be forged, which is a huge improvement over state-of-the-art where paper documents or scanned copies can indeed be easily forged.
All interactions with issuers and verifiers do not require the user to set or memorize any passwords. The requests pop up within the identity wallet and user simply has to accept or reject and authenticate using biometrics. The user can use the same wallet for all online service yet the transactions are completely private.
To sum up, the decentralized identity solution can use one identity wallet and allow users to seamless interact with various online providers with a complete frictionless experience. Stored credentials in the wallet can be easily reproduced and be used to verify identity of the user, automatically fill lengthy forms, thereby reduce customer onboarding time significantly and cut customer acquisition costs. So decentralized identity not only addresses all the pain points mentioned above but also provides other value additions that make it a very attractive solution.
Love decentralized identity ? Subscribe to get notified of my future posts that will dig deeper into this topic.


